Recent Posts

Does GitHub Enterprise Cloud Make Your Organisation Less Secure?
GitHub’s oAuth scopes could leave organisations vulnerable.
Your Terraform Module Needs an Opinion
Learn why your Terraform modules should be opinionated.

A Rube Goldberg Machine for Container Workflows
Learn how can you securely copy container images from GHCR to ECR.

Parameter Store vs Secrets Manager
Which AWS managed service is best for storing and managing your secrets?

A Lost Parcel Results in a New Website
When Australia Post lost a parcel, we found a lot of problems with one of their websites.
We Have a New Website (Finally)
After 15 years we rebuilt our website. Learn more about the new site.
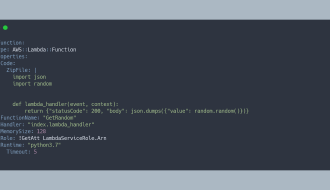
If You're not Using YAML for CloudFormation Templates, You're Doing it Wrong
Learn why you should be using YAML in your CloudFormation templates.

Logging Step Functions to CloudWatch
A quick guide on how to stream AWS Step Function logs to AWS CloudWatch.

Zoom's Make or Break Moment
Covid-19 has fuelled massive growth for Zoom. Will this motivate them to fix their security problems?


